Why FFT Perimeter Intrusion Solutions Are Essential for Effective Surveillance
Why FFT Perimeter Intrusion Solutions Are Essential for Effective Surveillance
Blog Article
Recognizing the Value of Information and Network Safety and security in Today's Digital Age
In an era where electronic makeover is integral to service success, the importance of information and network safety has never ever been extra pronounced. As companies progressively incorporate innovative technologies, they also subject themselves to a myriad of cyber threats that can compromise delicate details and disrupt procedures. Recognizing the consequences of information violations, along with the necessary safety actions required to alleviate these risks, comes to be crucial. The difficulty exists not just in implementing these measures but likewise in growing an aggressive safety and security society within companies. This conversation will certainly explore these intricacies further and disclose vital insights on securing electronic possessions.
The Surge of Cyber Hazards
The landscape of electronic safety and security has actually come to be progressively dangerous as cyber dangers proliferate internationally. Organizations throughout various industries are dealing with a surge in advanced assaults, varying from ransomware to phishing systems. These hazards not just jeopardize sensitive data however also interfere with organization operations, leading to significant economic losses and reputational damage.
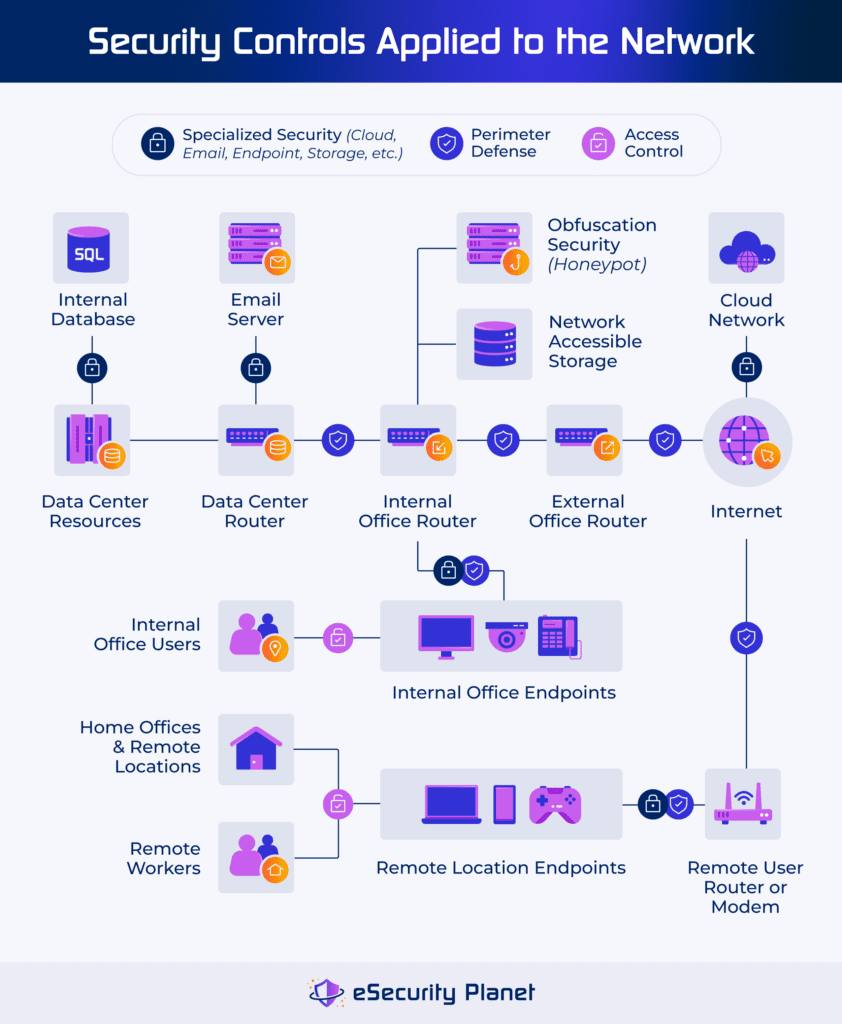
Moreover, the development of advanced techniques such as expert system and device knowing has actually equipped enemies with the tools to automate their procedures, making it progressively testing for traditional security actions to maintain speed. As organizations navigate this treacherous landscape, the urgency for durable information and network safety strategies has actually never ever been higher, highlighting the requirement for vigilant tracking, timely updates, and worker recognition to mitigate these escalating dangers.
Effects of Information Breaches
Information breaches can have severe and far-reaching ramifications for organizations, influencing not only their financial standing however likewise their trustworthiness and client depend on. When delicate information is endangered, companies commonly encounter direct financial losses because of legal costs, regulatory penalties, and the expenses related to occurrence feedback. Additionally, the long-term effects can be also much more harmful; a tarnished reputation might lead to lost organization chances and declining client retention.
The erosion of customer trust is probably one of the most perilous repercussion of an information violation. Clients might doubt a company's capability to secure their personal information and, consequently, might select to take their organization somewhere else. This loss of self-confidence can cause lowered earnings and market share.
Furthermore, organizations might experience increased examination from regulators and stakeholders, causing an extra challenging operational environment. The mental influence on staff members, who may really feel less safe or valued, can likewise impact productivity and spirits.

Important Safety Measures
Carrying out important safety and security procedures is important for safeguarding sensitive info and maintaining business honesty. Organizations should adopt a multi-layered safety method that encompasses both physical and digital safeguards.
One of the foundational measures is to establish durable access controls, making sure that only accredited employees can access sensitive data. This can be attained through strong password plans, multi-factor verification, and normal audits of user accessibility civil liberties. In addition, securing information both in transportation and at rest supplies a vital layer of defense against unapproved accessibility.
Routine software application updates and spot monitoring are additionally vital, as they aid minimize vulnerabilities that might be manipulated Visit This Link by destructive stars. Organizations must carry out firewall softwares and intrusion detection systems to monitor network web traffic and recognize potential threats proactively.
Moreover, conducting regular safety analyses and infiltration screening enables organizations to recognize weaknesses in their defenses prior to they can be exploited. Employee training on protection recognition is similarly important, as human mistake continues to be one of the leading sources of information breaches. By integrating these essential protection steps, companies can significantly lower their danger exposure and improve their strength versus cyber risks.
Structure a Safety Society
Developing an effective safety culture within a company is a crucial enhance to implementing robust security actions. A security culture promotes an atmosphere where employees understand the significance of protecting sensitive details and are proactively taken part in guarding it. This culture is grown via extensive training programs that highlight the significance of information security and the possible threats connected with oversight.
Management plays a vital role in developing this society. When execs prioritize safety and demonstrate their dedication, employees are more probable to embrace comparable attitudes (data and network security). Routine communication concerning safety procedures, updates, and policies makes sure that every person remains enlightened and vigilant
Motivating open dialogue about protection worries empowers workers to report questionable activities without anxiety of vengeance. Carrying out an incentives system for positive behavior can better incentivize people to take possession of security practices.
Furthermore, carrying out simulations and drills assists strengthen the relevance of preparedness and action. By incorporating safety into Related Site day-to-day procedures and decision-making procedures, organizations can create a resilient workforce with the ability of adjusting to evolving hazards. Inevitably, a strong protection culture not just secures data yet additionally improves general organizational stability and reliability.
Future Trends in Information Protection
Arising innovations and advancing cyber threats are improving the landscape of information protection, prompting organizations to adjust their methods as necessary. One significant fad is the enhanced fostering of synthetic intelligence (AI) and maker discovering (ML) for threat discovery and reaction. These technologies enable even more aggressive protection procedures by evaluating vast quantities of data to recognize anomalies and prospective breaches in real-time.
Another pattern is the relocation towards zero-trust safety and security versions, which operate under the concept that no individual or gadget need to be relied on by default. This technique emphasizes constant verification and lessens accessibility to sensitive data based upon strict verification processes.
Furthermore, the increase of remote work has actually accelerated the demand for robust endpoint safety solutions that protect gadgets outside typical network boundaries - data and network security. As organizations accept cloud computer, protecting information en route and at rest has actually become vital, bring about the development of advanced security methods
Conclusion
In conclusion, the significance of information and network security can not be overemphasized in the modern electronic landscape. As cyber dangers continue to escalate, companies should remain proactive and attentive in carrying out extensive security actions. The possible consequences of data violations highlight the need of securing sensitive information. Cultivating a culture of safety understanding and adapting to arising patterns will certainly enhance strength against evolving cyber hazards, inevitably ensuring the defense of beneficial properties and preserving stakeholder trust.
In an era where electronic improvement is integral to business success, the relevance of information and network security has never been a lot more noticable. Recognizing the consequences of information violations, alongside the crucial protection steps needed to mitigate these risks, becomes important.Producing an effective safety and security society within an organization is an important complement to implementing robust protection actions.Emerging innovations and advancing cyber hazards are reshaping the landscape of information safety and security, motivating companies to adapt their imp source approaches appropriately.In final thought, the significance of information and network safety and security can not be overstated in the contemporary digital landscape.
Report this page